Integrating with OneLogin
![]()
![]()
![]()
Before starting the integration process, you must have requested, and been approved for, an Onshape Enterprise account or trial, and have an Onshape Enterprise domain name.
An example of an Enterprise domain name might be: MyCompanyName.onshape.com.
Note that you are only able to use one SSO provider at a time.
This configuration process might fail without parameter values customized for your organization. Use your custom SSO identity provider (for example: Okta, PingOne, or ClassLink) dashboard to add Onshape as an application and record the values that are specific for your organization. You need those values for the following procedure.
Onshape signs all outgoing SAML certification requests. You are not required to upload any certificates (for example, a SAML signing certificate), except in the case of ADFS integration because ADFS validates incoming SAML requests. Note that Microsoft also recommends migration from the latest version of ADFS to Microsoft Entra ID. See ADFS Overview for more information.
Typically, an SSO provider is set up for one Enterprise. If setting up a multi-tenant configuration (an SSO provider with multiple Enterprises) using SAML 2.0, the Administrator must use com.onshape.saml2.sp.<domain prefix> as the Onshape Entity ID, and check the Use entityid with company domain prefix box. See the "Configuring the SSO provider in Onshape" section below.
OneLogin SSO setup for Onshape
Sign into the OneLogin administration panel to setup a new app connector to Onshape. Go to <yourdomain>.onelogin.com/admin.
Add new application
- Select Applications from the top navigation bar.
- Select Applications.
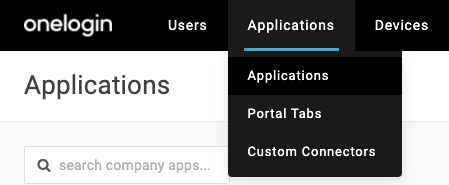
- Click Add App in the upper right corner.
- Search for SAML.
-
Select SAML Test Connector (Advanced).
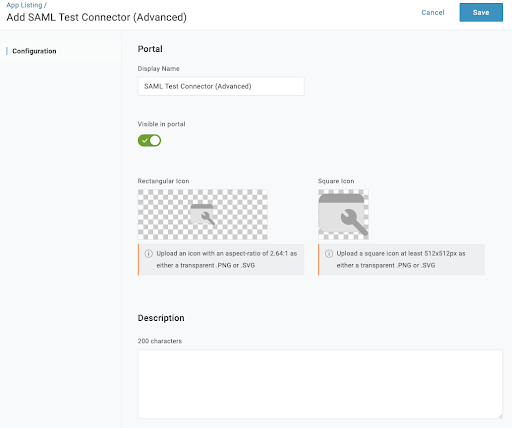
- Set the Display Name as "Onshape" and use any applicable icons.
- Click Save.
Configuration
Once the application is saved, there are more options that will be available for modification. This next section will setup important application details for the integration. Details about each section can be found on the Test connector configuration page.
- RelayState: Leave blank
- Audience (EntityID): com.onshape.saml2.sp
- Recipient: https://cad.onshape.com/identity/saml2/sso
- ACS (Consumer) URL Validator*: https://cad.onshape.com/identity/saml2/sso$
- ACS (Consumer) URL*: https://cad.onshape.com/identity/saml2/sso
- Single Logout URL: https://<custom_onshape_domain>.onshape.com
- Login URL: https://<custom_onshape_domain>.onshape.com
- SAML not valid before: 3 (Default value)
- SAML no valid on or after: 3 (Default value)
- SAML initiator: OneLogin (this is if you want your portal page to sign directly in)
- SAML nameID format: Email
- SAML issuer type: Specific
- SAML signature element: Assertion
- Encrypt assertion: (Unchecked)
- SAML encryption method: TRIPLEDES-CBC (Default)
- Sign SLO Response: (Unchecked)
- SAML sessionNotOnOrAfter: 1440 (Default)
- Generate Attribute Value tag for empty values: (Checked)
- Sign SLO Request: (Unchecked)
Parameters
This should be configured to pass the appropriate information over to Onshape during the SSO handshake. These values are as follows:
- NameID value: Email (Default value)
-
companyName: Macro type (type in the custom domain name into the field), for example, in a domain that is "company.onshape.com" enter only "company" in this field
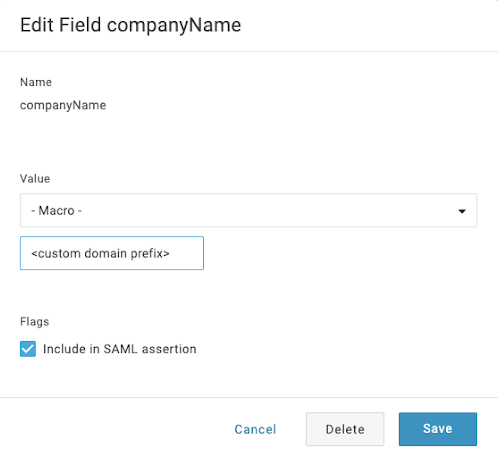
- firstName: Map to First Name and include in SAML assertion
- lastName: Map to Last Name and include in SAML assertion
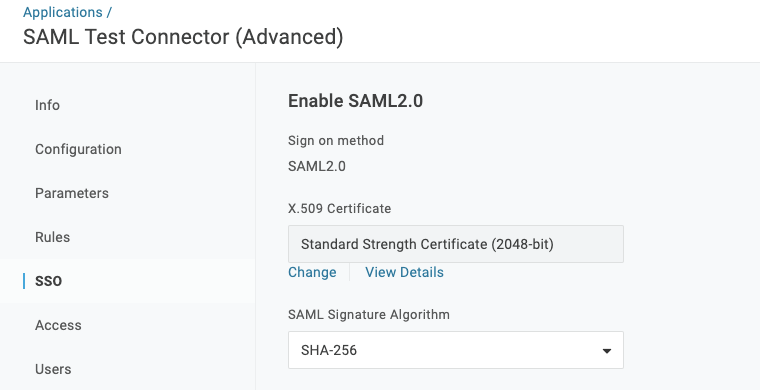
SSO
Here, you will have to set only the SAML Signature Algorithm option.
Download the SAML Metadata
Now that OneLogin is configured and saved, in the upper right corner, pull down the More Actions menu and select SAML Metadata, which downloads an XML file to your local machine. This file will be used in the set up of OneLogin in the Onshape Enterprise Authentication settings.
Configure the SSO Provider in Onshape
Once Onshape is configured in the identity provider and you have downloaded the identity provider's metadata file (referred to in Onshape as the configuration file), the SSO provider can be configured in Onshape.
The example images below shows a generic identity provider being configured, but the steps are the same for all identity providers.
- Sign in to your Onshape Enterprise account, using your specialized domain name, as an administrator.
Select
Enterprise settings
from your account:
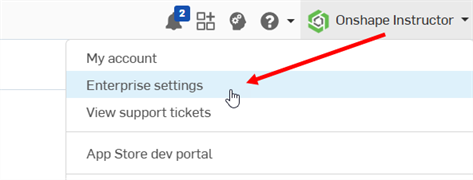
- Select Authentication from the left navigation menu.
-
In the Single sign-on (SSO) subsection, click the Configure SSO provider button:
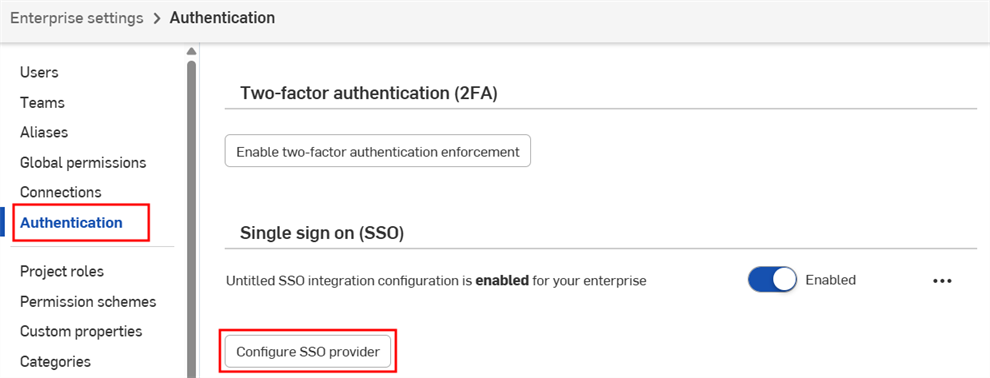
-
The Create SSO provider dialog opens:
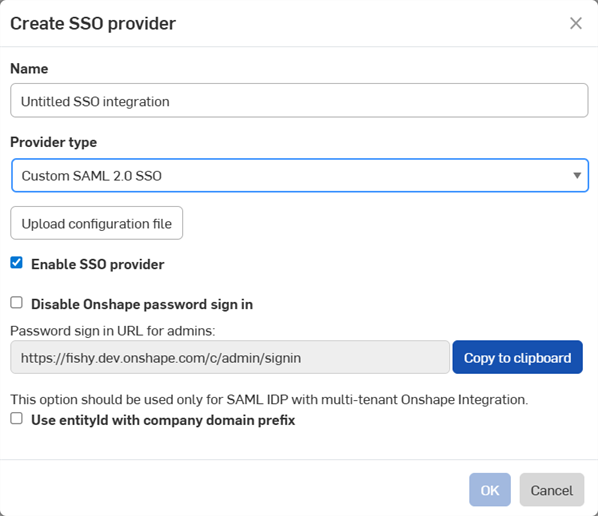
-
In the Name field, enter name, such as Custom SSO
-
In the Provider type dropdown, select your SSO provider from the list.
-
Leave Enable SSO provider checked.
-
Leave Disable Onshape password sign in unchecked for the moment.
-
Check Use entityid with company domain prefix if you have a multi-tenant setup (an SSO provider with multiple Enterprises).
-
Click the Upload configuration file button:
Disable Onshape password sign in disables the typical Onshape password sign in for you and your users. Only the SSO provider sign in prompt is displayed for the Onshape URL. Before checking this option, ensure you can sign in to Onshape yourself (as administrator). You can return here later and enable it once sign in through your SSO provider is verified to work correctly.
Choosing to enforce signing in to Onshape via SSO also results in users not being able to sign in to non-enterprise domains directly, such as cad.onshape.com.
Typically, an SSO provider is set up for one Enterprise. If setting up a multi-tenant configuration (an SSO provider with multiple Enterprises) using SAML 2.0, the Administrator must use com.onshape.saml2.sp.<domain prefix> as the Onshape Entity ID, and check the Use entityid with company domain prefix box.
-
-
Locate and select the metadata configuration file you downloaded previously, and click Open:
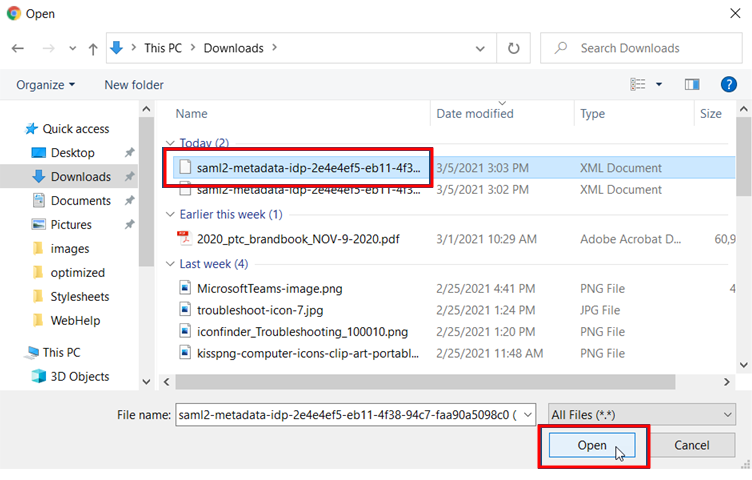
-
Click OK:
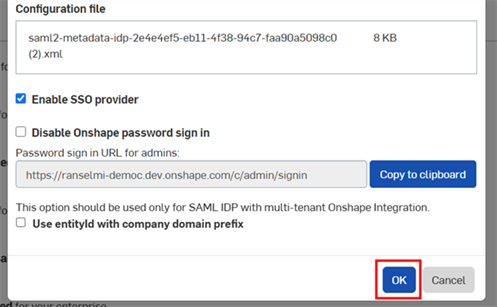
-
The file is uploaded. A notification appears when the upload is completed:
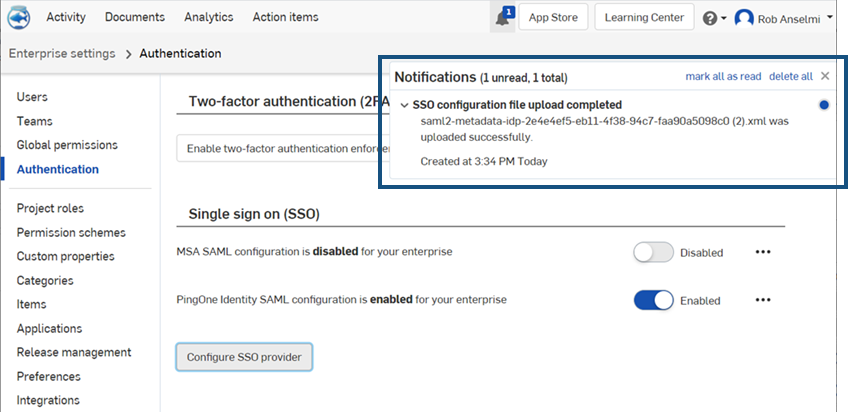
- Sign out of both your Onshape and SSO provider accounts. Be sure to do a hard refresh of both accounts. When you reach the Onshape sign-in page once again, the page has a new
Sign in
link at the bottom, for your SSO provider.
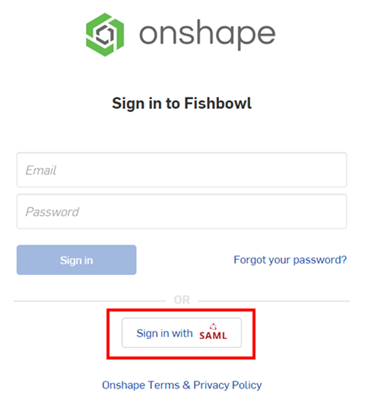
In order to sign in to Onshape, administrators must provision their users (in their single sign on account) to use the Onshape application.