PingOne との統合
![]()
![]()
![]()
統合プロセスを開始する前に、Onshape Enterprise アカウントまたは試用版を要求し、承認され、Onshape Enterprise ドメイン名を持っている必要があります。
Enterprise ドメイン名は、たとえば MyCompanyName.onshape.com のような形になります。
一度に使用できる SSO プロバイダーは 1 つだけであることに注意してください。
このコンフィギュレーションプロセスは、組織用にカスタマイズしたパラメータ値がないと失敗することがあります。カスタム SSO ID プロバイダー (Okta、PingOne、ClassLink など) ダッシュボードを使用して、Onshape をアプリケーションとして追加し、組織に固有の値を記録します。次の手順では、これらの値が必要です。
Onshape は、送信されるすべての SAML 証明書リクエストに署名します。ADFS は受信した SAML リクエストを検証するため、ADFS 統合の場合を除き、証明書 (SAML 署名証明書など) をアップロードする必要はありません。Microsoft では、最新バージョンの ADFS から Microsoft Entra ID への移行も推奨しています。詳細は、ADFS の概要を参照してください。
通常、1 つの Enterprise に 1 つの SSO プロバイダーを設定します。SAML 2.0 を使用してマルチテナントコンフィギュレーション (複数の Enterprise がある SSO プロバイダー) を設定する場合、管理者は com.onshape.saml2.sp.<ドメインプレフィックス> を Onshape エンティティ ID として使用し、[entityId を Company のドメインプレフィックスに使用] チェックボックスをオンにする必要があります。以下の「Onshape での SSO プロバイダーの構成」セクションを参照してください。
Onshape を PingOne シングルサインオンアカウントに追加する
Company シングルサインオンを有効にするには、まず PingOne シングルサインオンアカウントに Onshape アプリケーションを追加する必要があります。
-
管理者として PingOne ポータルにサインインします。左側のナビゲーションペインで、[接続] アイコンをクリックします。
-
[アプリケーションの追加] をクリックします。
![[アプリケーションの追加] ボタンが表示された [PingIdentity アプリケーション] ページ](Resources/Images/SSO/PingOne-Step-003.png)
-
[Web アプリケーション] ボックスをクリックします。次に、SAML 接続タイプの右側にある [構成] ボタンをクリックします。
![[Web アプリ] ボックスをクリックし、[SAML 接続タイプ] ダイアログの [構成] ボタンをクリックする](Resources/Images/SSO/PingOne-Step-006.png)
-
開いている[アプリケーションプロファイルの作成] タブで、アプリケーション名と説明を入力します。次に、ペインの下部にある [次へ] ボタンをクリックします。
![アプリケーション名と説明が記載された [アプリケーションプロファイルの作成] ページ](Resources/Images/SSO/PingOne-Step-007.png)
-
開いている [SAMLの構成] タブで、ACS URL フィールドに https://cad.onshape.com/identity/saml2/sso と入力します。
-
同じタブで下にスクロールして、[エンティティ ID] フィールドに com.onshape.saml2.sp、[アサーション有効期間 (秒)] フィールドに 300 と入力します。次に、[保存して続行する] ボタンをクリックします。
![[PingIdentity Onshape アプリケーション] ページ。エンティティ ID とアサーションの有効性が概説されている。](Resources/Images/SSO/PingOne-Step-009.png)
-
[マップ属性] タブで、[PingOne ユーザー属性] ドロップダウンリストから電子メールアドレスを選択します。
![SAML 属性の概要が表示された [属性のマッピング] ページ](Resources/Images/SSO/PingOne-Step-010.png)
-
同じタブで、次の 3 つの SAML 属性を作成します。
-
[属性の追加] リンクをクリックし、ドロップダウンリストから [静的属性] を選択します。これにより最初の静的属性が作成されます。[静的キー] フィールドに firstName、[静的値] フィールドに名を入力します。
-
[属性の追加] リンクを再度クリックし、ドロップダウンリストから [静的属性] を選択します。これにより、2 番目の静的属性が作成されます。[静的キー] フィールドに lastName、[静的値] フィールドに姓を入力します。
-
[属性の追加] リンクを再度クリックし、ドロップダウンリストから [静的属性] を選択します。これにより、3 番目の静的属性が作成されます。[静的キー] フィールドに、companyName、[静的値] フィールドにドメイン名プレフィックスを入力します。たとえば、Onshape Enterprise 名が fishbowl.onshape.com の場合は、Fishbowl と入力します。
![[SAML 属性] ページから [静的属性] を選択する](Resources/Images/SSO/PingOne-Step-011.png)
-
-
3 つの SAML 属性がすべて入力されると、下の画像のようになります。[保存して閉じる] ボタンをクリックします。
![[SAML 属性] ページの [属性のマッピング]](Resources/Images/SSO/PingOne-Step-012.png)
-
「アプリケーション」ウィンドウが開きます。[平均デイリーサインオン] スイッチをクリックして、アプリケーションへのサインオンを有効にします。アプリケーションが正常に保存されたことを示す通知が右上隅に表示されます。
![[平均デイリーサインオン] をオンにするスイッチが表示されている [アプリケーション] ページ](Resources/Images/SSO/PingOne-Step-014.png)
-
[コンフィギュレーション] サブセクションをクリックします。次に、[ダウンロード] ボタンをクリックして、メタデータファイルをダウンロードします。このファイルが正常にダウンロードされると、右上にメッセージが表示されます。メッセージを閉じるには、 X をクリックします。
![[アプリケーション] ページで [構成]、[メタデータファイルのダウンロード] の順にクリックする](Resources/Images/SSO/PingOne-Step-016.png)
![PingIdentity ページ、左側のナビゲーションバーから [接続] をクリック](Resources/Images/SSO/PingOne-Step-002.png)
上記の ACS の URL は、Onshape Enterprise の URL ではなく「cad.onshape.com」である必要があります。
![メタデータファイルの概要を含む [SAML 接続の構成] ページ](Resources/Images/SSO/PingOne-Step-008.png)
Onshape での SSO プロバイダーの構成
ID プロバイダーで Onshape を構成し、ID プロバイダーのメタデータファイル (Onshape ではコンフィギュレーションファイルと呼びます) をダウンロードしたら、Onshape で SSO プロバイダーを構成できます。
以下の画像の例は、構成中の汎用 ID プロバイダーを示していますが、手順はすべての ID プロバイダーで同じです。
- 専用のドメイン名を使用して、管理者として Onshape Enterprise アカウントにサインインします。アカウントから Enterprise 設定を選択します。
![[マイアカウント] メニューに移動し、[Enterprise 設定] ボタンをクリックする](Resources/Images/SSO/azure-sso-025-02-01.png)
- 左側のナビゲーションメニューから [認証] を選択します。
-
[シングルサインオン (SSO)] サブセクションで、[SSO プロバイダーを構成] ボタンをクリックします。
![[シングルサインオン (SSO)] 設定の [SSO プロバイダーを構成] をクリックする](Resources/Images/SSO/azure-sso-027-02.png)
-
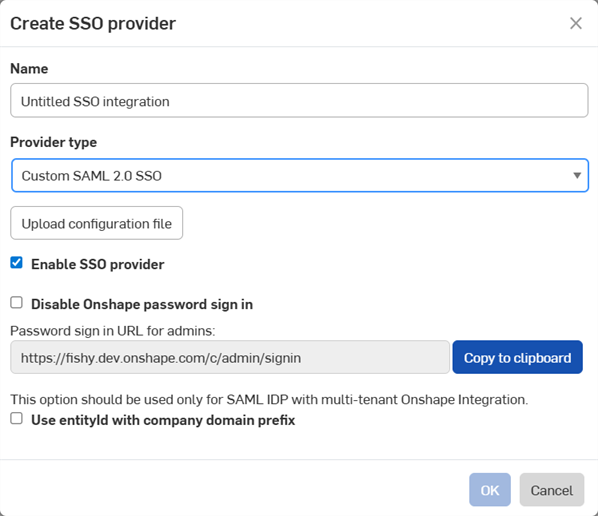
SSO プロバイダーを作成ダイアログが開きます。
-
[名前] フィールドに、カスタム SSO などの名前を入力します。
-
[プロバイダータイプ] ドロップダウンで、一覧から SSO プロバイダーを選択します。
-
[SSO プロバイダーを有効化] はオンのままにします。
-
今のところ、[Onshape パスワードによるサインインを無効にする] チェックはオフのままにしておきます。
-
マルチテナント設定 (複数の Enterprise を持つ SSO プロバイダー) を使用している場合は、[Company ドメインプレフィックス付きのエンティティ ID を使用] をオンにします。
-
[コンフィギュレーションファイルをアップロード] ボタンをクリックします。
[Onshape パスワードによるサインインを無効にする] をオンにすると、自分とユーザーの通常の Onshape パスワードサインインが無効になります。Onshape の URL には SSO プロバイダーのサインインプロンプトのみが表示されます。このオプションをチェックする前に、管理者として Onshape にサインインできることを確認してください。SSO プロバイダーからのサインインが正しく機能することが確認されたら、後でここに戻って有効にできます。
SSO を介した Onshape サインインの強制を選択すると、ユーザーは cad.onshape.com などの Enterprise 以外のドメインに直接サインインできなくなります。
通常、1 つの Enterprise に SSO プロバイダーをセットアップします。SAML 2.0 を使用してマルチテナントコンフィギュレーション (複数の Enterprise がある SSO プロバイダー) をセットアップする場合、管理者は com.onshape.saml2.sp.<ドメインプレフィックス> を Onshape エンティティ ID として使用し、[entityId を Company のドメインプレフィックスに使用] チェックボックスをオンにする必要があります。
-
-
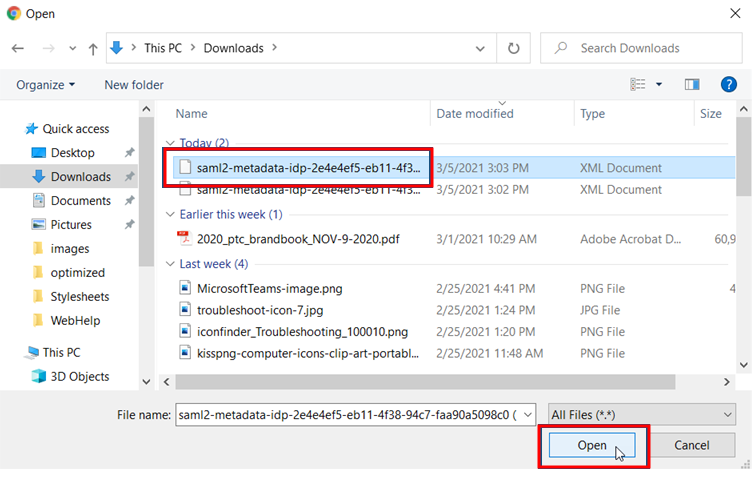
以前にダウンロードしたメタデータコンフィギュレーションファイルを探して選択し、[開く] をクリックします。
-
[OK] をクリックします。
![[OK] をクリックして SSO プロバイダーの作成を完了させる](Resources/Images/SSO/custom-sso-03-02.png)
-
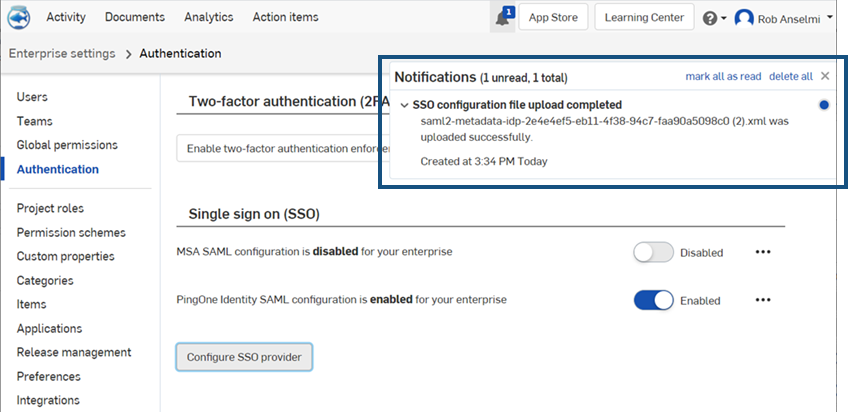
ファイルがアップロードされます。アップロードが完了すると、通知が表示されます。
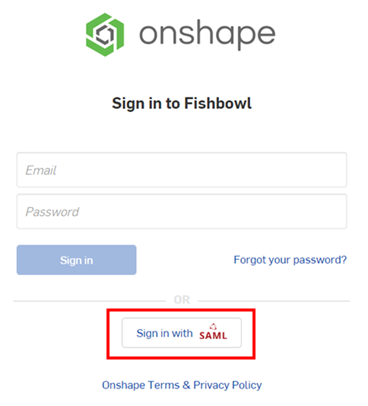
- Onshape アカウントと SSO プロバイダーアカウントの両方からサインアウトします。両方のアカウントを必ず更新してください。Onshape のサインインページに再度アクセスすると、ページの下部に SSO プロバイダー用の新しい [サインイン] リンクが表示されます。
Onshape にサインインするには、管理者は Onshape アプリケーションを使用するために (シングルサインオンアカウントで) ユーザーをプロビジョニングする必要があります。